How to: Install BurpSuite CA certificate on Android 14+ with Magisk (No third-party modules)
Intro
It’s that time of the year when I finally remembered my password from this website and started dumping notes from 2025. There is already a number of ways to do this through the third-party Magisk modules:
But did you know you can create your own and its likely faster than clicking stuff in Magisk to add a third party module?
Custom Magisk module to add system BurpSuite CA certificate
This method is based on this atricle.
You’d start with the usual steps of getting the Burp’s CA from its proxy listening address, converting it to PEM and uploading it to the phone:
1
2
3
4
5
6
7
8
9
10
11
12
BURP_PROXY_ADDRESS="http://localhost:8080"
wget "$BURP_PROXY_ADDRESS/cert" -O cacert.der
openssl x509 -inform DER -in cacert.der -out cacert.pem
CACERT_HASH=$(openssl x509 -inform PEM -subject_hash_old -in cacert.pem | head -1)
CACERT_NAME="$CACERT_HASH.0"
echo $CACERT_NAME
mv cacert.pem $CACERT_NAME
adb push $CACERT_NAME /sdcard/Download
Next, we drop into ADB shell, make some folders and put our cert in them! Et voila! It is that easy:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
adb shell
su
CACERT_NAME="9a5ba575.0" # replace me with the value in the first script
MAGISK_MODULE_NAME="writable_system"
# create our own magisk module dir and corresponding directory structure
cd /data/adb/modules/
mkdir -p "$MAGISK_MODULE_NAME/system/etc/security/cacerts/"
# copy original system CA certs to module dir
cp /system/etc/security/cacerts/* "$MAGISK_MODULE_NAME/system/etc/security/cacerts/"
# copy burp CA to module dir
mv "/sdcard/Download/$CACERT_NAME" "$MAGISK_MODULE_NAME/system/etc/security/cacerts/"
# set proper permissions over the burp certificate
cd "$MAGISK_MODULE_NAME/system/etc/security/cacerts/"
chown root:root $CACERT_NAME
chmod 644 $CACERT_NAME
# exit the adb shell
exit
exit
# reboot the phone
adb reboot
Our Magisk module is, in fact, a directory under /data/adb/modules containing files that will replace the original OS data after load. You don’t even need to create any module manifest of any sort for this to work.
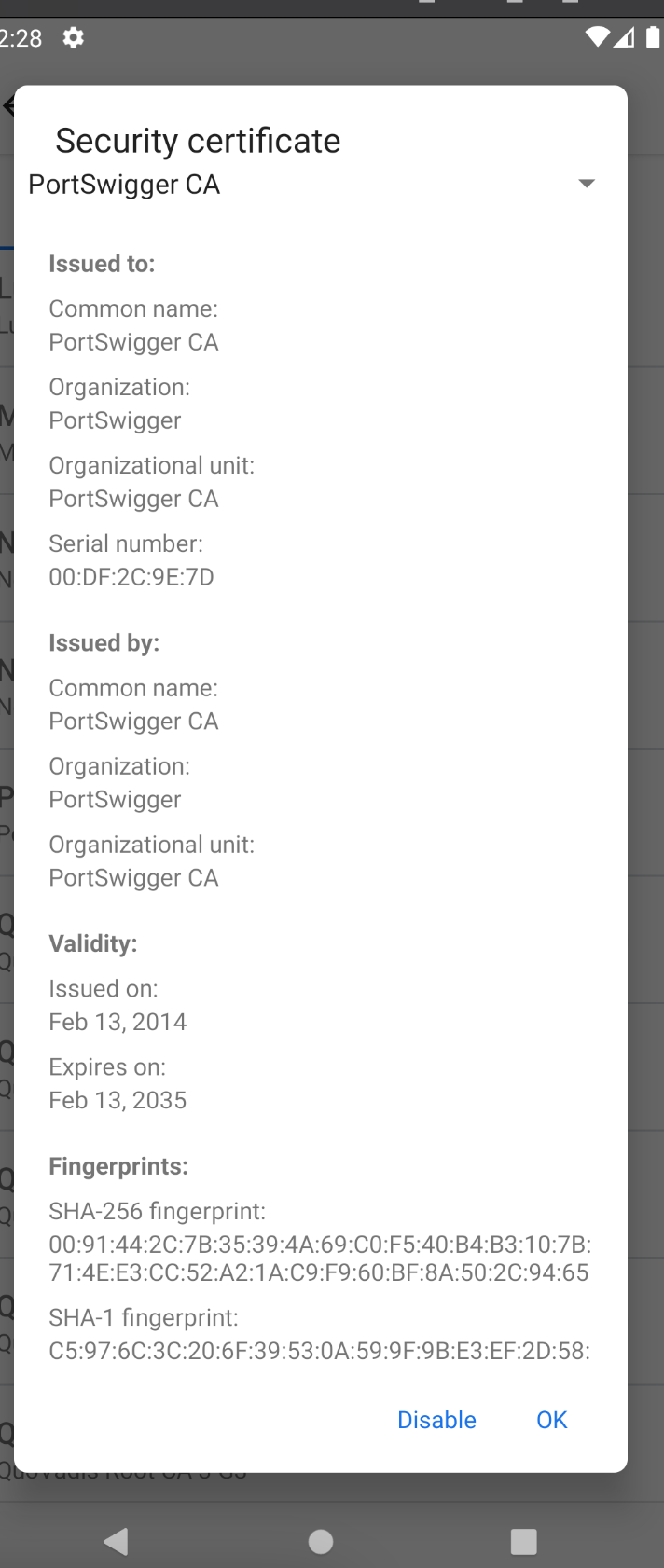
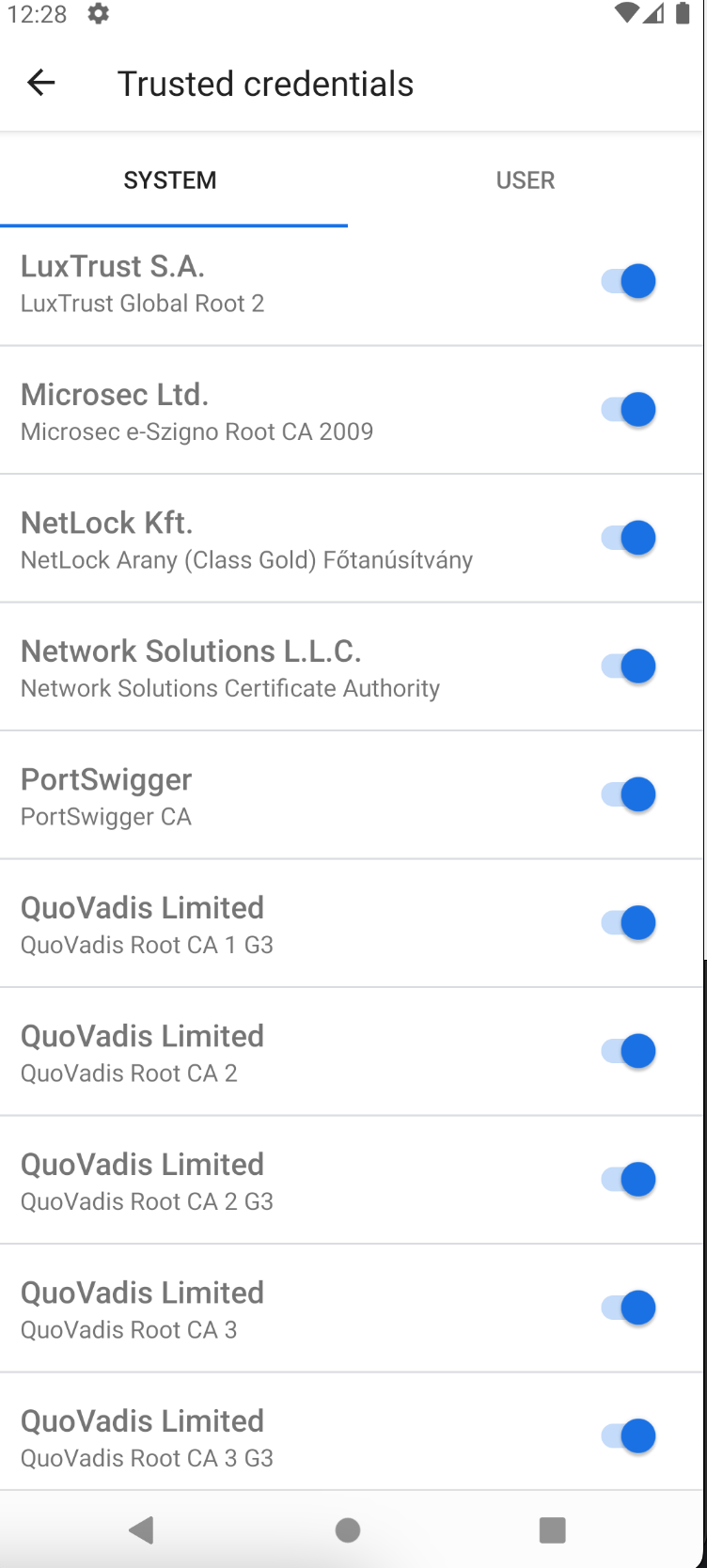
Once the above commands are executed and the phone reboots, you will see your Portswigger CA installed on the phone, just like in the old times: